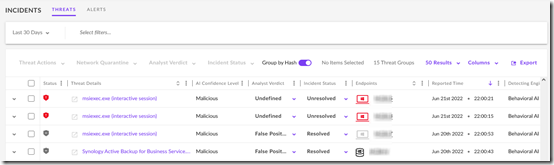
I’ve been testing SentinelOne as an advanced anti-virus system (EDR). Currently it’s only in Detect mode while I see how it behaves in my environment.
There were several false positives detected by file scans that were easily handled. However when I installed the Synology Active Backup for Business (ABB) Agent, that was flagged as malicious not because of the file hash but because of the way the program behaved.
Even after marking one of the detections as a False Positive, SentinelOne continued to flag Active Backup on other devices:
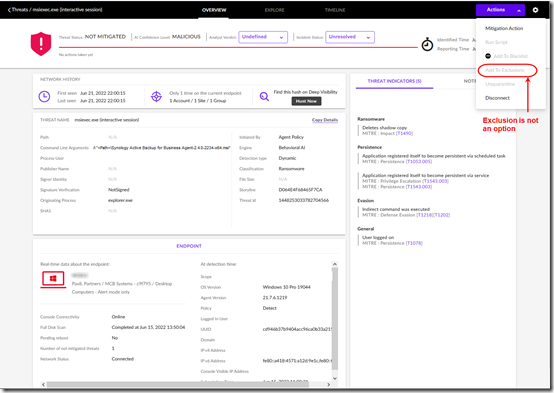
The SentinelOne knowledge base is only available to subscribers, so I won’t post links here. I did find the article “Best Practices – Handling False Positives.” It suggests adding exclusions from the threat details, but that is not possible on a behavioral detection—the option is grayed out in the UI.
The right column of that screen shot also shows the behaviors that were flagged as malicious. The threat itself is named “msiexec.exe” (the Microsoft Windows Installer executable), so obviously I can’t exclude that. The command line (edited in the graphic to show the important part) showed the Active Backup Agent installer was the culprit.
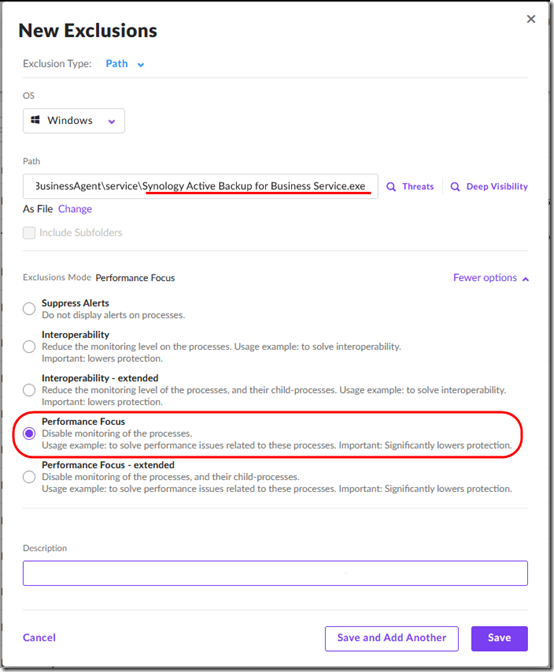
I contacted support to ask if I needed to exclude the path to the Active Backup installer, and if I would need to update exclusion that every time a new installer was released. To my surprise, they replied that I should add a Performance Focus exclusion on “Synology Active Backup for Business Service.exe”.
Determining What to Exclude
Sure enough, that seems to prevent further alerts, but why? Support said the exclusion was determined after reviewing the Process Tree Timeline. This confused me at first—how am I supposed to look at the 43,806 events in the Process Tree Timeline and know which file to exclude? However after reviewing the SentinelOne article titled “Incident Details – Explore,” I think I have an idea.
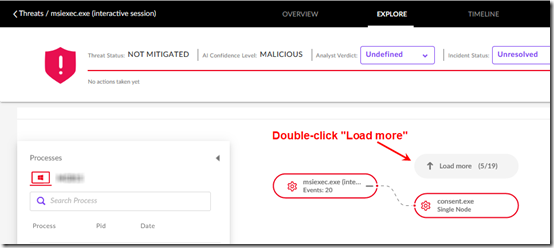
1. In the SentinelOne dashboard, open the Incidents page, then open the Threat Details page for one of the malicious detections. Click the Explore tab at the top to see the events related to the “dynamic threat” (detected by the Behavioral AI engine).
2. Ignore the huge list of events at the bottom.
3. In the top part of the page, keep double-clicking Load more to the right of the root process until all of the follow-on processes are loaded. Click and drag the tree to move it around.
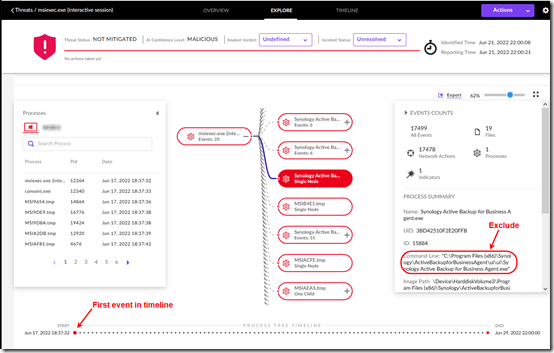
4. You should now have a relatively finite number of detected processes, 19 in this case. Hover over processes to see their full names and where they fall in the timeline (the dots across the bottom). You can also click the Plus sign to see sub-processes, but that doesn’t seem relevant here.
I see lots of instances of Synology Active Backup for Business Service. One of the “Single Node” processes seems to be the first event in the timeline (if that matters?).
5. Single-click on a process to see Process Details in a fly-out pane to the right. The command line shows the full path to the process.
6. In the dashboard, go to Sentinels then choose the Exclusions tab. Add a New Exclusion with Exclusion type “Path” for OS “Windows”. After filling in the Path, click More options and choose Performance Focus. Save the exclusion.
Install the Active Backup for Business Agent on a new machine with SentinelOne running and confirm that it is not flagged as malicious.