This month, Microsoft is re-fixing an NTLM Relay Attack vulnerability and recommending additional mitigations on some servers. I checked how Server 2016 with Essentials is affected.
This article describes additional mitigations:
KB5005413: Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS)
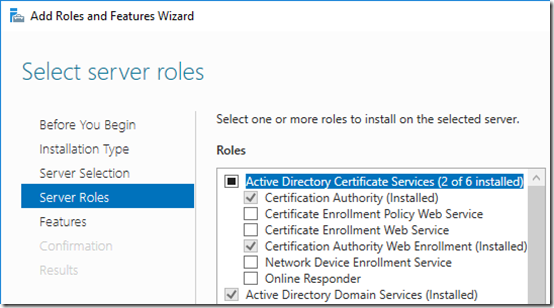
You are potentially vulnerable to this attack if you are using Active Directory Certificate Services (AD CS) with any of the following services:
Certificate Authority Web Enrollment
Certificate Enrollment Web Service
Checking an Essentials 2016, machine, the first service is installed but the second is not:
I’m not sure why Essentials enables Web Enrollment—I’ve never used a web site to request or update a certificate. But just in case it is used in some Essentials process (perhaps setting up connection from client computers, or setting up Anywhere Access), I’ll leave it enabled and apply the suggested mitigation. We’ll see if that breaks anything.
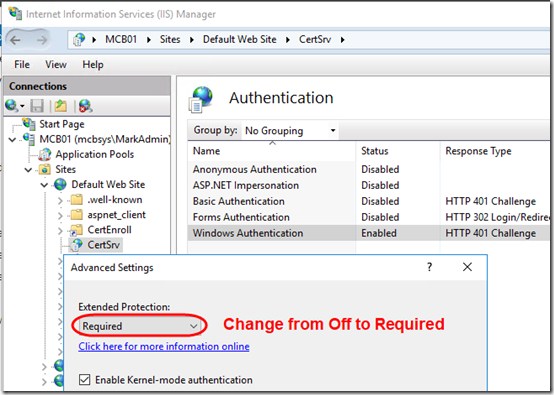
Certificate Authority Web Enrollment does require two updates in IIS. In the Default Web Site, CertSrv application, go to Authentication > Windows Authentication > Advanced and set Extended Protection setting to Required:
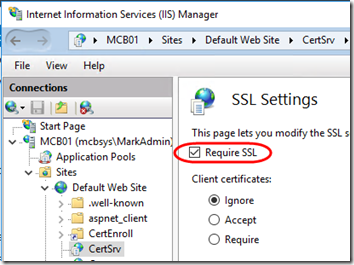
Also set the CertSrv application, go to SSL Settings, check Require SSL, then click Apply:
I restarted IIS with “iisreset” to make sure the changes take effect:
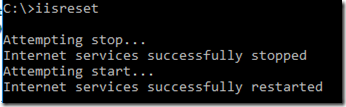
Note that because Certificate Enrollment Web Service is not enabled, step 2 of the article is not required.
I also made the same changes in a Server 2012 R2 Essentials machine.
I’m afraid that the secondary mitigation, disabling NTLM authentication entirely, would be more disruptive, so I’m not going to tackle that at this point.