I’m testing Synology Surveillance Station on an older DS214se running DSM 6.2.4-255556. I wanted to see how the remote view app works on Android. The documentation is thin but I think with the help of a tcpdump packet trace (run as SSH with sudo against the NAS), I’m finally getting an idea what is going on.
To eliminate port forwarding as an issue, I connect the phone to Wi-Fi on the same internal network as the NAS. I also turned off HTTPS in DS cam, to make sure it connects directly to the IP address.
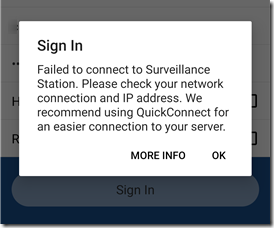
But it still fails to connect:
The tcpdump command:
tcpdump -i eth0 -s 65535 -w /volume1/homes/admin/tcp.pkt
In the packet trace, I see this:
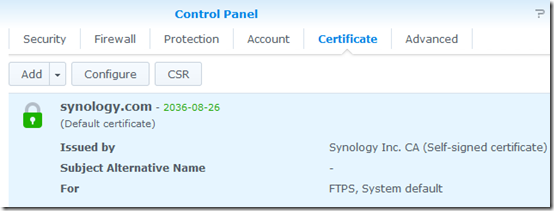
The NAS already has a self-signed security certificate:
So apparently the Android app doesn’t trust self-signed Synology certificates. In fact, it doesn’t even say that the certificate is the problem, just that the login failed.
Wait, why is it doing a TLS handshake when HTTPS is turned off?
Aha! A little earlier in the packet trace, I see a “302 Moved temporarily”:
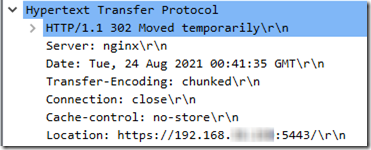
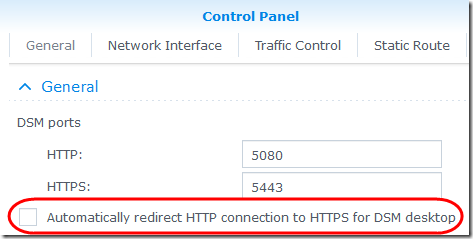
So the Synology setting that prefers HTTPS is actually forcing the DS cam logon to use HTTPS, which fails because the self-signed certificate is not trusted. I’m unchecking this under Control Panel > Network:
Sigh, login still fails. This time, the “moved temporarily” goes to port 5080, but it is still attempting TLS authentication and it is still failing on an invalid certificate. I don’t understand why, when HTTPS is deselected, why TLS is required.
I’ll open a Synology ticket and see what they suggest.
Update August 25, 2021
I tried installing the Synology self-signed certificate on my Android 10 phone, but when I used the certificate as downloaded from a web browser, I got the error “Private key required to install a certificate.” Apparently Android now requires that the certificate self-identify as a Certification Authority (CA: TRUE), See this StackExchange answer. The web browser certificate does not have that.
However I was able to download a certificate package directly from the NAS (Control Panel > Securitiy > Certificate, then click the down-arrow next to Add and select Export certificate). I extracted syno-ca-cert.pem, which does have the CA: TRUE attribute
The output of openssl.exe x509 -in syno-ca-cert.pem –text includes this:
![]()
I then converted it to a DER format using openssl:
openssl x509 -inform PEM -outform DER –in syno-ca-cert.pem -out syno-ca-cert.crt
At that point, I was able to import it to Android.
After all that, I’m still getting a connection error! In the stack trace, it now looks like the SSL handshake is succeeding (no more fatal “certificate unknown” message), but the login fails just the same.
Another Synology NAS – And the Fix
I had an even older Synology DS213 on hand. When I tried connecting DS cam to this unit, it provided a much more sensible message: the connection is untrusted; would you like to proceed?
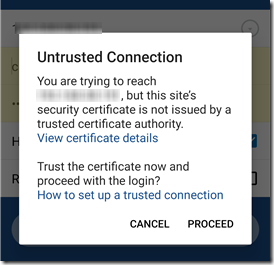
I chose Proceed, and DS cam connected. The certificate is then shown in the Android Security settings as a User certificate.
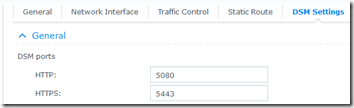
But wait, that unit connects on the default port 5001. I changed the default ports on my DS214se, probably for security reasons. At Control Panel > Network > DSM Settings, the ports are now configured as 5080 and 5443:
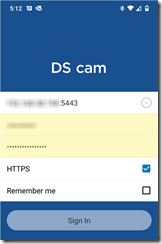
Sure enough, when I added “:5443” to the end of the address in DS cam, it connected to the first NAS just fine.
We saw above that the DSM was redirecting to port 5443, but for some reason, DS cam wouldn’t follow the redirect. Specifying the port explicitly in DS cam works.
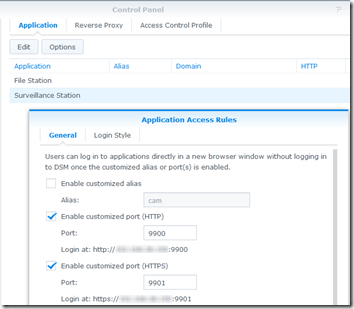
It is also possible to specify custom ports just for Surveillance station under Control Panel > Application Portal > Surveillance Station:
If you do that, specify :9901 when logging in from DS cam. I like this option as it allows me to open Surveillance Station for remote viewing without opening the rest of the NAS services.
Connect from Outside the Firewall
I’ve been testing from inside the firewall to make sure I wasn’t having a firewall issue. Now that that is working, I tried from outside the firewall, using a custom domain name and port forwarding. I only forwarded port 9901 in my router. I had to approve the untrusted certificate again, but after that, it worked fine, whether I connected from Wi-Fi or with cellular data. The only thing that doesn’t work—and this is not a new problem—is connecting from a guest Wi-Fi network when the NAS is on a different VLAN behind the same firewall. Communicating across VLANs is intentionally disallowed unless I set up a firewall exception.