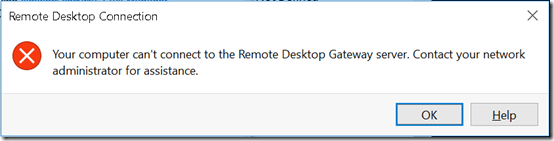
A new Windows 10 Pro 1803 computer could not establish a connection through a Server 2016 machine running Remote Desktop Gateway. The Win10 machine showed this error:
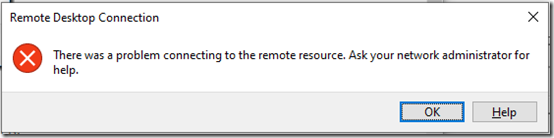
Update November 27, 2021 Had an almost identical error with a new laptop running Windows 10 21H!. The message was slightly different:
Also in 2021 (and maybe in 2018), on the client, in the Microsoft-Windows-TerminalServices-RDPClient/Operational event log, there is EventID 1026, “RDP ClientActiveX has been disconnected (Reason= 50331656)”.
In both cases, the server’s Security event log had a 4625 Audit Failure event with Status 0xC000035B:
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 12/14/2018 1:49:08 PM Event ID: 4625 Task Category: Logon Level: Information Keywords: Audit Failure User: N/A Computer: MyServer.mydomain.local Description: An account failed to log on. Subject: Security ID: NULL SID Account Name: - Account Domain: - Logon ID: 0x0 Logon Type: 3 Account For Which Logon Failed: Security ID: NULL SID Account Name: User1 Account Domain: mydomain Failure Information: Failure Reason: An Error occured during Logon. Status: 0xC000035B Sub Status: 0x0 Process Information: Caller Process ID: 0x0 Caller Process Name: - Network Information: Workstation Name: WIN10PRO-LAPTOP Source Network Address: xxx.xxx.xxx.xxx Source Port: 60469 Detailed Authentication Information: Logon Process: Authentication Package: NTLM Transited Services: - Package Name (NTLM only): - Key Length: 0
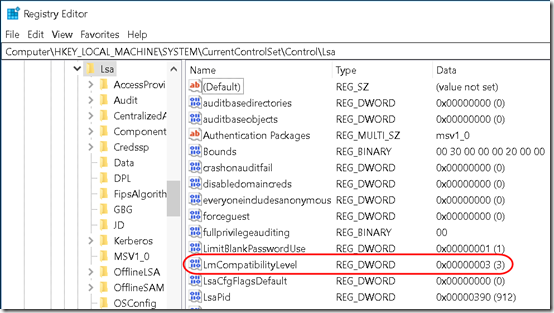
KB2903333 identifies this as a channel binding issue because the client is forcing NTLMv1. It recommends setting the LmCompatibilityLevel registry value to 3 or higher. (The article incorrectly refers to the LmCompatibility registry value. The correct name is LmCompatibilityLevel.)
I was skeptical of this as the cause because another off-site computer has LmCompatibilityLevel of 0 and connects through the same gateway without issues.
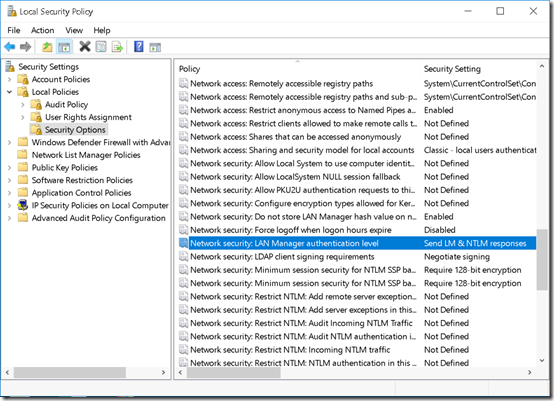
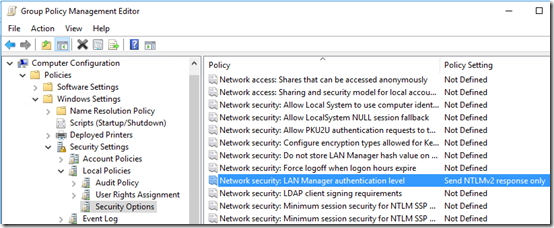
LmCompatibilityLevel can also be set in Local Security Policy by changing the Network security; LAN Manager authentication level:
I changed that to Send NTLMv2 response only:
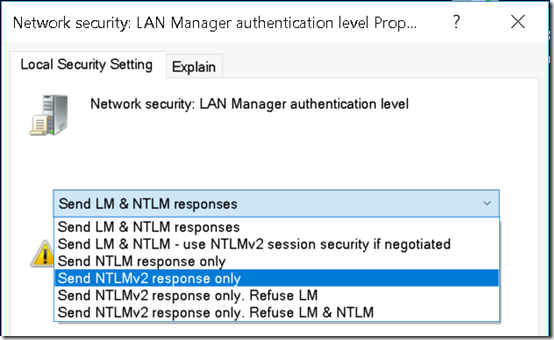
This changed the registry value HKLM\SYSTEM\CurrentControlSet\Control\Lsa\LmCompatibilityLevel to 3:
Once I’d made that change (no reboot required), I was able to log on from this computer through the gateway to an office computer.
What is still unclear is why this setting is only required on some client computers. However, considering how much time I’ve spent spinning my wheels on this issue, I think I’ll just set up a group policy to set Send NTLMv2 response only on all machines in the network:
Computer Configuration > Policies > Windows Setting . Security Settings > Local Policies > Security Options > Network security; LAN Manager authentication level – Send NTLMv2 response only
Server Side
KB2903333 mentions that the other option is to set this registry value to 0:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\TerminalServerGateway\Config\Core\EnforceChannelBinding
That would disable the Channel Binding requirement, which seems like it’s not a good idea. My server does not have that registry value, so it’s using the default of EnforceChannelBinding turned on.

THANK YOU!!! I’ve been looking for this for days to figure out why I couldn’t connect to a RDWebApp. This started randomly on only my PC. Thank you so much for this. Changed the LmCompatabilityLevel to 3 and it worked instantly.