I wanted to get TLS connections working between remote Grandstream phones connected over the Internet to a Grandstream UCM6102 PBX. This location already has an SSL certificate for its web site issued by a public Certification Authority. Here’s how to set up TLS with that kind of certificate.
You can use the same SSL certificate that you use for your web server since the web server and TLS operate on different ports from each other. Your router will direct web traffic on port 443 to the web server and TLS traffic on port 5061 to the UCM device.
Prepare the Certificate
This is the tricky bit. Basically the UCM (running Asterisk) works like an Apache server when it comes to certificates. This means you need the certificate in PEM format, saved as a .crt file, and you need the corresponding private key in PEM format in a separate .key file.
It’s possible that your Certification Authority already provided files in the required format, in which case you can skip this section.
What I had was a Windows-style .pfx file which included both the certificate and the private key. This was exported from the Windows server certmgr.msc after I had installed the certificate on the Windows web server (IIS).
I found this helpful article on how to use OpenSSL on a Windows machine to convert a .pfx file to the required certificate and private key files. Yes, you’ll need to download and install OpenSSL if you don’t have it already. Run the following commands at a command prompt. You’ll be prompted for the password you used when you exported the .pfx file, and when extracting the private key, for a password to use to encrypt the key:
Extract the certificate:
openssl.exe pkcs12 -in myCert.pfx -clcerts -nokeys -out myCert.crt
Extract the key, save as an encrypted key:
openssl.exe pkcs12 -in myCert.pfx -nocerts -out myCert.encrypted.key
Decrypt the private key and save unencrypted:
openssl.exe rsa -in myCert.encrypted.key -out myCert.key
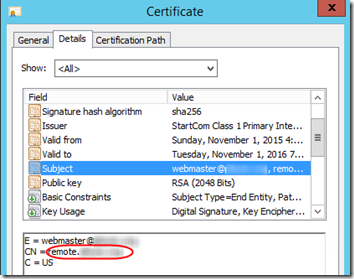
Get the Common Name of Your SSL Certificate
When you requested an SSL certificate, you told the Certification Authority what name the certificate should be valid for. To find that name, open the SSL certificate .crt file in Windows. On the Details tab, highlight the Subject. The value in the lower pane after “CN” is your certificate’s Common Name. In our case, I’ll call it remote.mydomain.com.
Your public DNS must point that common name to the network where the UCM is installed. If you’re already hosting a web server on the same network, the public DNS is probably already configured.
Set Up the Router
This assumes you have the UCM6xxx plugged in to a router that controls port forwarding.
By default, SIP traffic travels on UDP port 5060. That was getting a lot of hack attempts, so I closed 5060 that on the router.
TLS is an encrypted protocol. Encryption doesn’t work on the UDP protocol, so it uses TCP. Set TCP port 5061 to forward to the UCM.
Set Up the Phones
My test phone is a Grandstream GXP2130. In the account that should connect via TLS:
General Settings > SIP Server: remote.mydomain.com (the UCM’s Common Name)
SIP Settings > Basic Settings > SIP Transport: TLS/TCP
In the Grandstream Wave softphone app, the settings are similar:
(Ext. Number) > Edit Account > SIP Server: remote.mydomain.com
(Ext. Number) > SIP SETTINGS > Transmission Protocol: TLS
Set Up the UCM
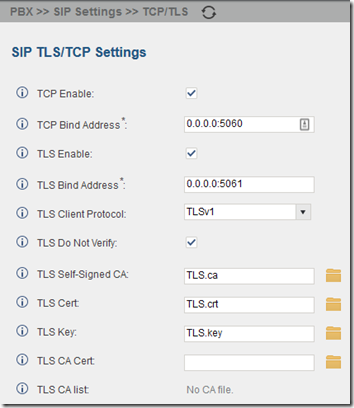
PBX > SIP Settings > TCP/TLS
TCP Enable: checked
TCP Bind Address: 0.0.0.0:5060
TLS Enable: checked
TLS Bind Address: 0.0.0.0:5061
TLS Client Protocol: TLSv1
TLS Do Not Verify: checked
TLS Cert: upload myCert.crt, extracted above
TLS Key: upload myCert.key, extracted above
Note that even after uploading, the UI still shows “TLS.crt” and “TLS.key”, not the names that you uploaded:
Assuming you are using a certificate issued by a well-known public Certification Authority, you should not need to upload a TLS Self-Signed CA or a TLS CA Cert.
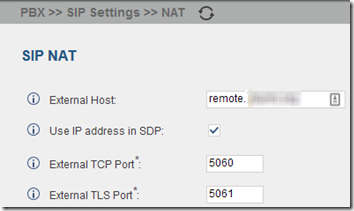
PBX > SIP Settings > NAT
External Host: remote.mydomain.com (the Common Name you determined above)
External TLS Port: 5061
After saving these changes and rebooting the router, you should be able to connect phones across the Internet using TLS.

Hi,
How did you verify that the voice connection is secured.
When we tick validate chain checking, the phone is unregistered
Pretty much followed your instructions apart from blocking 5060 UDP on the router
I don’t recall that I did verify a secure connection, but I think if you do a packet trace at the router, you could confirm that it’s doing a TLS handshake.
Take a packet capture on the UCM (Maintenance/Network troubleshooting/Ethernet capture), and open the downloaded log with Wireshark. There must be sign of transport layer security, used port and encryption between the phone and the UCM.