The hosted Exchange part of Office 365 has been performing pretty well once I got it configured. However, I continue to have issues with Forefront, a separate-but-integrated piece that sits in front of hosted Exchange. Compared to the Google Postini service I used previously, Forefront has given me more spam, false positives, a 3-day wait to see quarantine notices, and a separate quarantine email for each email alias. Since I still have my Postini account, I’ve decided to go back to Postini for spam and virus filtering. Here’s how I set that up.
Step 1: Tell Forefront to Allow Postini IPs
- Go to https://admin.messaging.microsoft.com and log in to your Forefront configuration. (If you’re using Firefox and get “Server Error in ‘/’ Application”, try Internet Explorer instead.)
- Click on the Administration tab. You should land on the Company sub-tab.
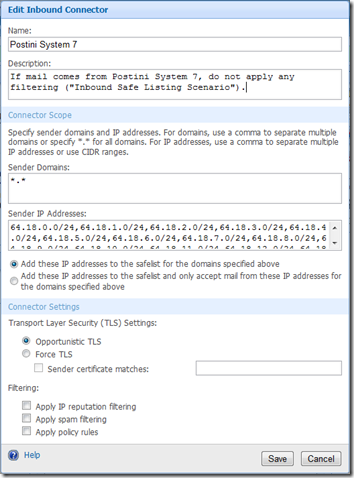
- Set up an Inbound Connector that tells Forefront to not do any filtering on mail coming from Postini. The Help calls this an Inbound Safe Listing Scenario. See the detailed example below.
- Click on the Domains sub-tab. Under Enabled Domains, click on your primary domain (not the yourdomain.onmicrosoft.com subdomain).
- Next to Inbound Connectors, click on Select, choose the connector you just defined, then click on OK. This applies that connector to your domain.
In order for the Inbound Connector to handle the mail, both the Sender Domains and the Sender IP Addresses must match.
Since we want mail from any domain to be handled by the connector, set Sender Domains to *.*.
We want to only accept mail from Postini’s servers. My Postini account is on Postini’s System 7 server, so the range of IP addresses that Postini may send from is 64.18.0.0 – 64.18.15.0. That translates to CIDR 64.18.0.0/20. Unfortunately, Forefront only allows CIDRs starting from /24, so you have to specify 16 CIDRs:
64.18.0.0/24, 64.18.1.0/24, 64.18.2.0/24, 64.18.3.0/24, 64.18.4.0/24, 64.18.5.0/24, 64.18.6.0/24, 64.18.7.0/24, 64.18.8.0/24, 64.18.9.0/24, 64.18.10.0/24, 64.18.11.0/24, 64.18.12.0/24, 64.18.13.0/24, 64.18.14.0/24, 64.18.15.0/24
The other trick is to uncheck the three Filtering boxes at the bottom of the dialog. Here’s an example of the complete Inbound Filter:
Note Be sure to find out what Postini system you are on. The example above only applies to System 7.
Step 2: Set Postini to Deliver Email to Office 365
- If you don’t remember your Office 365 “virtual server,” use nslookup or log in to your DNS provider to get the current MX record. It should be something like “mydomain-com.mail.eo.outlook.com”. Copy that destination server to the clipboard.
- Log in to your Postini admin page.
- Under Orgs and Users, Choose Org “[mydomain.com] Email Config 1”.
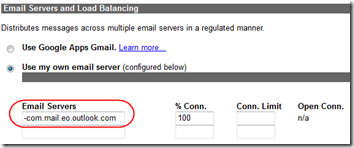
- Click on Inbound Servers > Delivery Manager > Edit.
- Change the Email Servers to point to your outlook.com virtual server.
Step 3: Update Your DNS to Point the MX to Postini
- Log in to your public DNS provider.
- Set the priority of the existing Office 365 MX record to 9. We’ll leave this in there for now in case the Postini routing doesn’t work.
- Add your four Postini MX records at priorities 0 through 3.
If you still have your original signup email from Postini, your MX records are listed there. If not, you’ll need to refer to this article to figure them out. Mine look like this:
1st priority record: mcbsys.com.s7a1.psmtp.com.
2nd priority record: mcbsys.com.s7a2.psmtp.com.
3rd priority record: mcbsys.com.s7b1.psmtp.com.
4th priority record: mcbsys.com.s7b2.psmtp.com.
Step 4: Test
Give the Forefront connector 45 minutes to propagate, and the DNS at least an hour. Send yourself some emails from an outside account (Yahoo, Gmail, whatever). Assuming that they get through, check the headers to see if they went through Postini. In the chain of “Received” servers, you should see that mail was received from something like “exprod7mx181.postini.com”. You should also see Postini’s spam measurements with headers like “x-pstn-neptune” and “xpstn-levels”.
The first stop in the chain after entering the Microsoft network should show that your Inbound Connector (“X-FOPE-CONNECTOR”) was applied, and should identify the sending Postini IP address in an “X-Safelisted-IP” header. The “X-Forefront-Antispam-Report” header is still there but apparently has no effect.
Step 5: Remove Office 365 from DNS
Once you are sure that all your mail is flowing through Postini to Office 365, you can update your public DNS to remove the priority 9 MX record left from Step 3. This will prevent spammers from directly targeting Office 365 by using out-of-sequence MX records.
Note The new Inbound Connector only handles mail that goes to your domain, which is now flowing through Postini. Mail sent directly to your Office 365 address ([email protected]) does not go through Postini so it still relies on Forefront for filtering.
Congratulations, your email is flowing through Postini. Look forward to a single, daily quarantine report that includes all your email aliases, and hopefully more accurate discernment of ham vs. spam.

Exactly what we are doing tomorrow after 2 months of excessive spam through Office365!!!
Simply amazing – been asking Office 365 tech support if this was possible for months…answer was always no….this works perfectly! One question tho – any way to route outbound mail through Postini (in addition to the incoming that this article addresses?)
JP, from a brief review of Postini’s help pages on Outbound Messaging (http://www.postini.com/webdocs/admin_ee_cu/wwhelp/wwhimpl/common/html/wwhelp.htm#href=ob_toc.html&single=true) and the PDF config guide (http://www.postini.com/webdocs/outbound/en/outbound_config_en.pdf), it looks like Postini is only designed to receive mail from servers, not directly from Outlook clients. So if you are willing to run an in-house mail server, and use Postini as a smart host, you could send outbound mail to your server, which would then forward it through Postini. I don’t know, but somewhat doubt, that O365 will let you direct outbound traffic from their servers back through Postini.
Thanks Mark – I was thinking more around perhaps setting up an Outbound connector to route all outgoing mail from Office 365 to Postini where outbound filtering would then apply. I’ve been playing around with this and it seems to be working to some degree. I need to verify several settings. Unfortunately we do not have an inside server, all of our clients connect to MS Office 365 Exchange.
Will routing like this work to route outbound through Postini? Outbound smart host scenario – FOPE acts as a smart host, redirecting outbound mail to an on-premises server that applies additional processing before delivering mail to its final destination. You may want to consider this option for your organization if you have an on-premises application or other compliance solution that you use to filter outgoing mail and you also want the benefits of FOPE edge, spam, virus, and policy filtering. For more information, see Outbound Smart Host Scenario.
http://technet.microsoft.com/en-us/library/gg430167.aspx
Interesting, very interesting. Will have to try this. So which SPF record is to be used with this configuration? The SPF record from Office 365 or the SPF record associated with Postini? I would assume the SPF from Office 365 as it’s still sending outbound mail.
Right – my SPF includes outlook.com, doesn’t mention Postini.
I know this is ressurecting an older post but can we use the postini FQDNs in those office 365 policies?
Luis, you’re thinking of using the Sender Domains instead of the Sender IPs? Interesting thought…especially if it allows wildcards and you could avoid having to enter 16 address blocks. I haven’t tried it–let us know if you do!
This is an old topic but I need to point out that you need to make sure you associate/enforce the new connector with your O365 domain, its not pointed out in this article.
http://technet.microsoft.com/en-us/library/gg430262.aspx
Also per JPs question, you cannot do reinjection as Postini will only attach if the domain allows open relay from the Postini System (which O365 will not)