I like to be able to review the Windows Security log to see who has logged on to a computer, among other things. This means that I need to audit Success as well as Failure events. However, with Windows 7 and 2008 R2, my old auditing policies are generating so many events that it takes a huge Security log just to hold one day’s worth of events. I finally dug in to audit subcategories to disable some overly verbose events.
Old Configuration
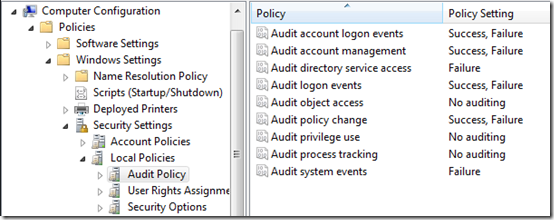
Here’s how I’ve had auditing set up going back to the SBS 2003 days:
Under Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy, I have the the following values:
For the time being, I’m still using those settings with XP and SBS 2008, so I’ve now applied this WMI filter to that old audit policy:
Name: WinXP/Vista/2003/2008
Description: XP=5.1.x – 2003=5.2.x – Vista/2008=6.0.x
Query:
select * from Win32_OperatingSystem
where (Version like "5.1.%") or (Version like "5.2.%") or (Version like "6.0.%")
(Vista and Server 2008 do allow subcategory configuration but it has to be configured locally with the auditpol command as explained here, or using scripts as shown in MSKB 921469.)
Audit by Subcategories
Before going any further, run these commands from a Windows 7 or 2008 R2 machine to view and save the current audit subcategories, which should reflect your old policy above:
auditpol /get /category:* > auditpolicy.txt
auditpol /backup /file:auditpolicy.backup.txt
You can re-run the first command to see if your policy updates are successful.
Create a New Group Policy Object
This TechNet article cautions against defining both basic and advanced audit settings, so for Windows 7 and Server 2008 R2, create a new GPO. You can create and edit the GPO on a Server 2008 R2 machine, or on a Windows 7 machine with the Remote Server Administration Tools (RSAT) installed.
Defining audit subcategories by group policy only works on Windows 7 and 2008 R2, so create a new WMI filter and assign it to the GPO:
Name: Win7/2008R2
Description: Windows 7 and Windows 2008 R2 are 6.1.x.
Query:
Select * from WIN32_OperatingSystem where Version like "6.1.%"
Enable Subcategory Override
Under Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options, set this value:
| Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings | Enabled |
This allows the subcategory settings that we will define below to override the top-level settings (explanation).
Set Up Subcategory Policies
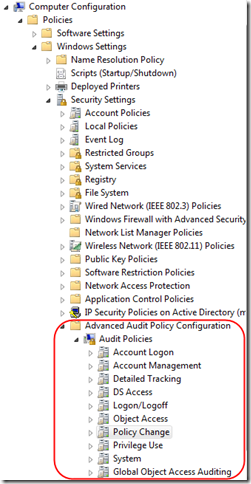
Under Computer Configuration > Policies > Windows Settings > Security Settings, go to the last item in the list, Advanced Audit Policy Configuration > Audit Policies:
As a starting point, use the output from auditpol that you generated above to set the policies in each category.
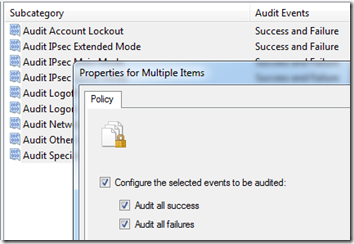
Tip To set all the policies in a group at once, select all the subcategories, right-click, and select Properties:
Define Subcategory Exceptions
Of course the whole point of setting up auditing by subcategory is to be able to exclude auditing on some particularly verbose events.
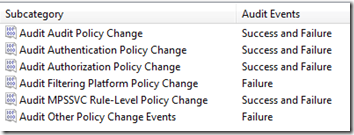
The main event that is filling my event logs seems to be 5447, “A Windows Filtering Platform filter has been changed.” The Task Category for this event is Other Policy Change Events, so under Audit Policies > Policy Change, I changed Audit Other Policy Change Events to Failure only. Then, because it looks related, I also changed Audit Filtering Platform Policy Change to Failure only.
Over time, I may choose to exclude some other events, but now that the group policy is in place, that’s a matter of a couple mouse clicks.

Thanks for sharing such informative resources.
With the same concern to audit GPO changes in my environment, I use Lepide auditor suite (http://www.lepide.com/lepideauditor/group-policy.html ) that works fantastic for me. It helps to get information regarding any created, deleted, renamed or modified object and alerts for any software policy modifications which can be detrimental to business.