When I set up a server for management via Remote Desktop, I prefer to change the RDP listening port to a non-default value (MSKB 306759) and to use a custom admin account for the logon. These simple obfuscations may not defeat a determined hacker, but they do reduce attacks from automated bots.
Of course, it’s not enough to just create an alternative admin account; you have to prevent the default Administrator account from logging on via Remote Desktop. Some go so far as to disable the Administrator account. I just block its remote access.
Domain Solution
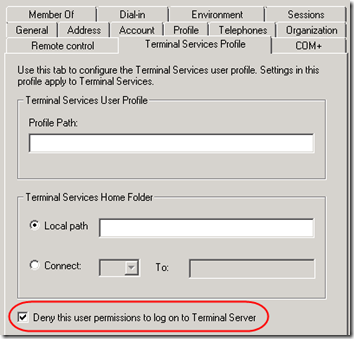
In a domain environment, you can use Active Directory Users and Computers to deny the Administrator access to Terminal Server.
Update 12/13/2010: The above worked in a 2003 domain but it does not work in 2008. Apparently in 2008, the Active Directory setting is only checked if the server is using Remote Desktop Services in Application Mode. To control RDP administrative access in a Server 2008 domain, use Local Security Policy as described for workgroups below. For more information, see MSKB 2258492, “You notice that the check box ‘Deny this user permissions to logon to a Remote Desktop Session Host Server’ behaves differently in Windows 2003 and Windows 2008.”
Workgroup Solution
But what if the server is only in a workgroup, e.g. a Hyper-V server where the domain controller is running as a guest? One simple solution is to remove the default behavior of granting all administrators remote access. Then, any user that needs remote access must be granted that privilege explicitly by adding the user to the Remote Desktop Users group.
Here’s how to do that on Windows Server 2008 R2:
1. Under Control Panel > User Accounts, click on Manage another account, then Create a new account. Set up the new account as an Administrator, then add a password.
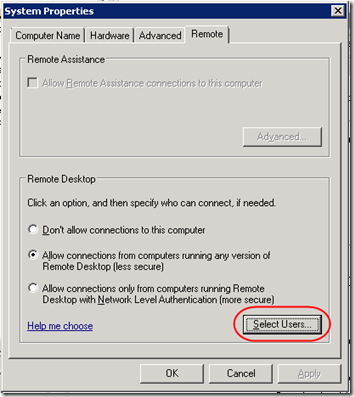
2. Right-click on Computer and select Properties. Click on Advanced System Properties. In the System Properties dialog, click on the Remote tab, then click the Select Users button. Add the new admin account to the list of Remote Desktop users. (This adds the user to the Remote Desktop Users group.)
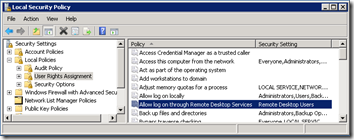
3. Select Start > Administrative Tools > Local Security Policy. Go to Security Settings > Local Policies > User Rights Assignment. Open the Allow log on through Remote Desktop Services policy and remove the Administrators item. When you are done, only Remote Desktop Users should have RDP access: