Today I did a disaster recovery test on my Windows Server 2008 R2 Hyper-V host. I used Windows Backup to do a bare metal restore of only the system volume. As expected, after the restore, the system volume was no longer encrypted. But even after re-encrypting the system volume, I was unable to set the data volumes to automatically unlock. Instead, it displayed “Data error (cyclic redundancy check).”
I decided to try the command line. Here I found that manage-bde –status listed two volumes out of about eight before aborting with the same error:
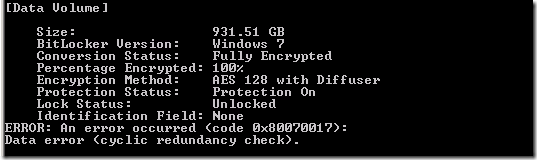
When I saw that error code 0x80070017 can mean that a file is missing or corrupt, it occurred to me that the old BitLocker auto-unlock keys are still on the restored system volume, but they cannot be accessed. So I tried manage-bde -autounlock -clearallkeys C:.
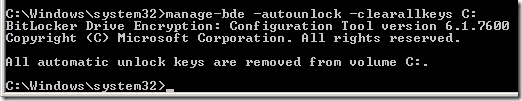
After this, manage-bde -status correctly lists all volumes, but manage-bde -autounlock -enable S: fails with the message:
ERROR: An error occurred (code 0x80310054):
The auto-unlock master key was not available from the operating system drive.
Maybe the master key will be re-created by a reboot? Sure enough, after rebooting and manually unlocking the drives again, I was finally able to enable auto-unlock on the encrypted data volumes.
System Volume Restore with BitLocker Data Volumes
Based on that experience, here is what I think should work next time for system volume restore:
- Do bare metal restore of system volume C:. The volume is restored unencrypted.
- Boot into OS and log in.
- From an administrative command prompt, run manage-bde -autounlock -clearallkeys C:.
- In the Control Panel, go to BitLocker Drive Encryption and enable Bitlocker on C:. Leave the encrypted data volumes in their locked state for now.
- Reboot to activate BitLocker. This apparently creates the auto-unlock master key on the system volume.
- Log in. In the Control Panel, go to BitLocker Drive Encryption and manually unlock encrypted data volumes.
- For each encrypted data volume, click on Manage BitLocker and set Automatically unlock this drive on this computer.
Update 02/17/2011: You may want to refer to the Manage-bde Parameter Reference on TechNet. Based on comments from Stephan (see below), a slightly modified procedure to try next time:
- Do bare metal restore of system volume C:. The volume is restored unencrypted.
- Boot into OS and log in.
- In the Control Panel, go to BitLocker Drive Encryption and enable Bitlocker on C:. Leave the encrypted data volumes in their locked state for now.
- Reboot to activate Bitlocker. This apparently creates the auto-unlock master key on the system volume. Log in.
- From an administrative command prompt, run manage-bde -autounlock -clearallkeys C:.
- In the Control Panel, go to BitLocker Drive Encryption and manually unlock encrypted data volumes.
- From a command prompt, check for and delete old External Keys on data volumes (I haven’t tested this!):
manage-bde -protectors -get S:
manage-bde -protectors -delete S: -type ExternalKey - Back in the Control Panel, for each encrypted data volume, click on Manage BitLocker and set Automatically unlock this drive on this computer.

Mark,
geart article and you really safed us a lot of work. I couldn’t find any information on the Microsoft web site how to deal with this CRC error and already thought I have to re-create all the encrypted volumes.
However, you might want to add that BitLocker will add a new external key that is required for autounlock feature. The old one can be deleted, e.g. before you re-enable autounlock:
manage-bde -protectors -delete S: -type ExternalKey
Chers,
Stephan
So “manage-bde -autounlock -clearallkeys C:.” doesn’t delete the old keys stored on the C: drive? I’m not familiar with the concept of “external keys” in Bitlocker.
Amazing, thank you. I came across this error after restoring the OS volume with Acronis True Image and then re-encrypting it. My second encrypted /storage/ volume would not auto-unlock and through a CRC error.
thanks, posted the solution on TechNet ;)
http://social.technet.microsoft.com/Forums/en-US/w7itprosecurity/thread/db7030e5-4c37-46dc-b0ea-492f3e1ef76f
Great work. You safed us a lot of work. Just one note: you have to enable BitLocker on the OS volume before you can clear the auto unlock keys and from my point of view it makes sense to delete the old External Key from the data volume before you enable the auto unlock featre again.
Stephan, glad you found it useful. I’ve posted a modified procedure based on your comments.
Ever heard of this happening?
I have an external hard drive, with two partitions, both of which I encrypted with Bitlocker.
The other day I noticed that the USB connection for that external drive had pulled out. Upon reconnection, when trying to open the drive ( the two partitions) it asked for the bitlocker key which I entered.
it says that the key is incorrect!!
Of course I tried this +MANY times – still no luck. I’ve always used the same key and am stumped ( and PO’d to say the least.
Does an encryption key reset to a default state when the hard drive is disconnected and then re-connected??
ANY IDEAS ARE VERY WELCOME!
Sorry Frank, I haven’t heard of that. You might try a post on the Windows 7 Security forum: http://social.technet.microsoft.com/Forums/en-US/w7itprosecurity/threads.
Thank you, work for win8 x64 too.
Thank you – worked for me, Win 8.1 64-bit, multiple SSD’s.
Pingback: Restoring a bitlocker system volume with Acronis 2014 | Thorsten on (mostly) Tech
Removing the external key worked great on server 2012, thanks!
Thanks, Mark Berry – a five year old post, but still very relevant. Helped me sort out my Windows 10 system! The revised instructions worked fine for me.
Still an epic post extremely helpfull with Windows 10 baremetal recovery (1809) tested
1: Baremetal recovery
2: Bitlocker C
when this is done completely:
3: manage-bde -autounlock -clearallkeys C:
4: manage-bde -protectors -delete D: -type ExternalKey
5: Enjoy Coffee :)
manage-bde -autounlock -clearallkeys C:
This worked for me!
You are da man!
A bit sad Windows can’t handle this on its own. But thanks a bunch!
Thanks for the great instructions. They solved my problem. Really appreciate the big help.
Awesome Post! I had planned to decrypt and re-encrypt all my drives until I saw this post. Worked like a charm! Thanks a million!!!
manage-bde -autounlock -clearallkeys C:
worked for me too!
Thanks for your help.
Best regards,
Johan.
https://martinvanbeurden.nl/blog/bitlocker-autounlock-error-0x80070017/
This is the clearest set of instructions I found anywhere