OpenLiteSpeed looks like a nice WordPress environment and I’ve been working on deploying the image found in the Azure marketplace. However I discovered that the image comes pre-configured with a user named Eric who has sudo privileges on the machine. This creates a back door for Eric to log in to any password-protected machine on Azure that runs OpenLiteSpeed.
Update This issue has been resolved—see the end of this post. If you are already using OpenLightSpeed for WordPress on Azure, use this post to check for the vulnerability and apply mitigations.
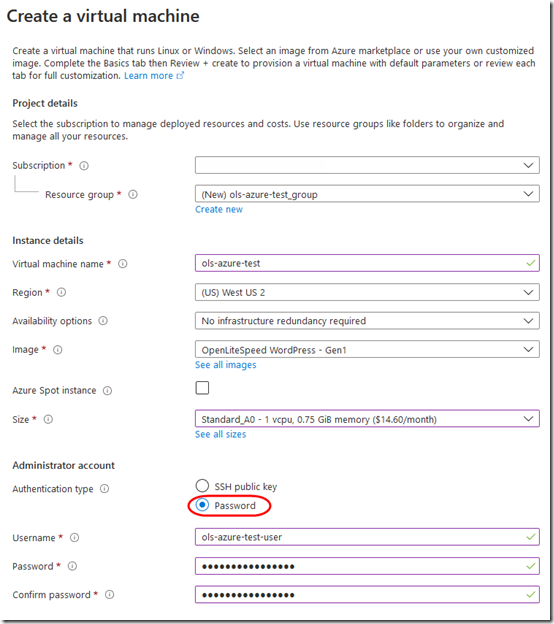
1. Create an openlitespeed-wordpress virtual machine on Azure:
Set it up for password logon:
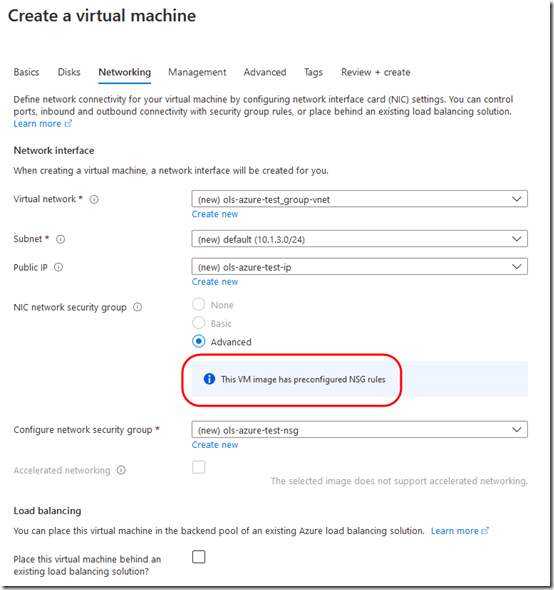
Note that you can’t change the network configuration:
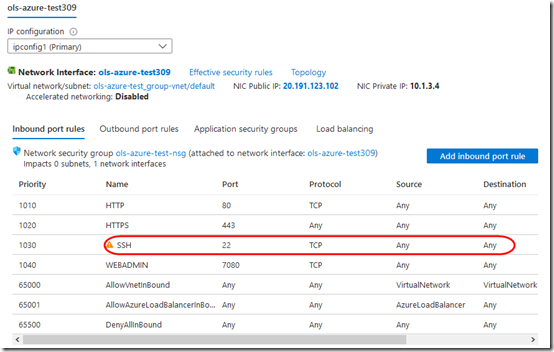
Once it’s created, you can see that SSH port 22 is open to all:
2. Connect to the machine with WinSCP and Putty.
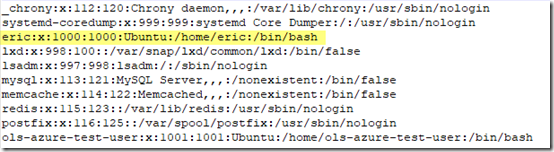
/etc/passwd is where I first noticed Eric, as user 1000:
/etc/shadow confirms he has a password:
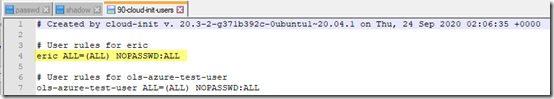
/etc/sudoers.d/90-cloud-init-users shows that he doesn’t need a password for sudo:
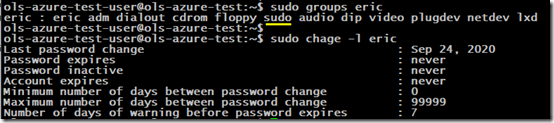
Eric is in the sudo group. His password never expires:
He has no home directory:
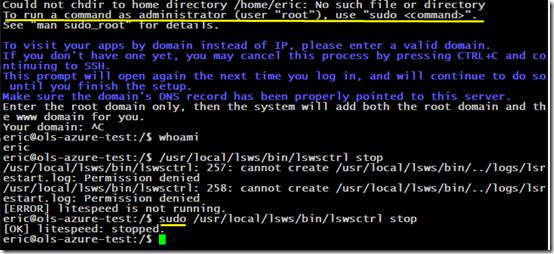
3. Change Eric’s password (sudo passwd eric), then log on as Eric. It works fine. Do something requiring sudo, e.g. shutting down OpenLiteSpeed. That works too.
Check for Other Traces of Eric
1. While logged on as the main user (not Eric), search for files owned by Eric. There shouldn’t be any.
sudo find / -user eric
2. Search for active processes owned by eric (there shouldn’t be any):
ps aux|grep -i eric
Note that this will always show a line for the grep process itself.
Mitigations
1. When first setting up the virtual machine, choose SSH authentication. This will disable password logon.
2. Use the Azure firewall to restrict port 22 to only your IP address. (This is a good idea regardless to prevent brute force SSH attacks.)
3. Change Eric’s password.
sudo passwd eric
4. Lock the password and expire all logons
sudo usermod --lock --expiredate 1970-01-02 eric
sudo chage -l eric
5. Open the /etc/sudoers.d/90-cloud-init-users file and comment out Eric’s line.
6. You can probably delete user Eric, but I haven’t tried this yet.
sudo deluser eric
Conclusion
This appears to be an honest mistake, not a malicious action. Still, Eric’s credentials need to be removed and a new image published. Users who have created virtual machines from this image need to be notified to remove Eric’s privileges. Hopefully LiteSpeed Technologies has saved the email addresses that it collects as the machine is created so that they can make this notification.
Update I shared this post privately with OpenLiteSpeed on December 21, 2020. Within two hours, they started fixing the vulnerability. An updated openlitespeed-wordpress image, with the vulnerability removed, went live on Azure on December 22. The only remaining artifact is the user Eric listed in /etc/sudoers.d/90-cloud-init-users, but since Eric is no longer defined as a user in the system, this should have no effect.