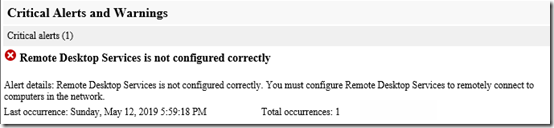
I’ve been testing Certify the Web on my Windows Server 2016 computer with the Essentials role. This sets up a Let’s Encrypt certificate for use as the server’s public certificate. Setup was pretty easy thanks to this great article on the Server Essentials site.Yesterday, two months after setup, the certificate renewed automatically. Awesome! But what is this message in this morning’s Health Report?
I logged on to the server, started the Remote Desktop Gateway Services manager, and was greeted with this message:
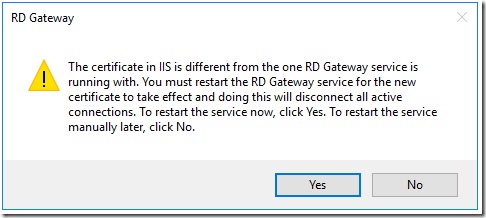
I chose NOT to restart yet.
Checking the Certificate Manager for the Local Computer, I see the new Let’s Encrypt certificate, expiring in three months.
Checking IIS > Server Certificates, I see the old and new certificates listed. When I browse to my server in Remote Web Access, the new certificate is being presented. And in fact the Certify the Web log shows these messages after the renewal:
2019-05-12 17:01:53.758 -07:00 [INF] Performing Automated Certificate Binding
2019-05-12 17:01:54.992 -07:00 [INF] Completed certificate request and automated bindings update (IIS)
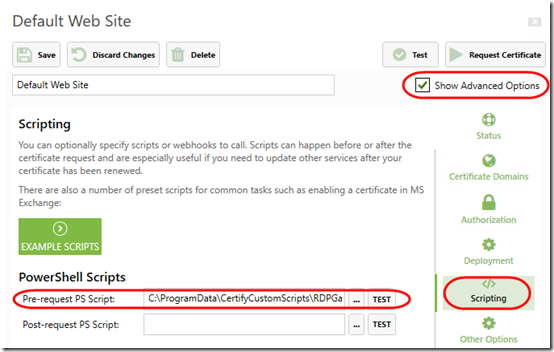
What seems to have been missed is the post-request script hook that I created to restart the Remote Desktop Gateway service. Oh! I see now that although I customized the script, I did not actually link it under Advanced Options > Scripting in Certify the Web. Here is how to set that up (put the script in a custom path to avoid it being overwritten when Certify the Web is updated):
Update July 12, 2019 Put this the second box, Post-request PS Script! See update below.
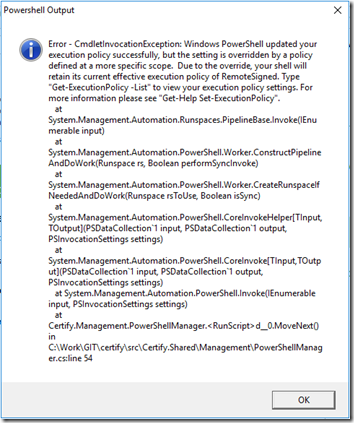
All fixed! Wait, not so fast. When I click Test, I get this message:
Looks like that is related to this bug: https://github.com/webprofusion/certify/issues/442. Certify the Web was trying to Set-ExecutionPolicy Unrestricted and my policy is more restrictive. That was reported on version 4.1.4 and a new version was expected in a week (from 20 February 2019). But I’m running 4.1.5 and still seeing the same issue.
I updated to the latest version, 4.1.6, and got the same error. Then the original GitHub poster suggested this workaround:
Change %programdata%\Certify\serviceconfig.json. I changed the powershellexecutionpolicy line to
“PowershellExecutionPolicy”: “RemoteSigned”
I had some inconsistent results when I tested that but I’ll leave it like that for now and hope it works.
Update July 12, 2019
My certificate auto-renewed yesterday. Today I again had the RDS gateway certificate errors.
This time when I clicked Test next to the script, it worked fine:
Checking Remote Desktop Gateway Manager, the new certificate was correctly registered. So script worked.
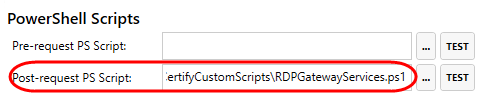
But wait, why is the script in the Pre-request PS Script box? It’s supposed to run after the new certificate is available! Moving it to Post-request PS Script now. Hopefully that fixes it for next time:
Update September 20, 2021
Today my scheduled tasks took me to check whether Certify the Web had successfully renewed the Let’s Encrypt certificate. (I’ve been doing this every two months based on the Let’s Encrypt certificate lifespan.) Yes, the certificate was renewed successfully and the post-request hook must have run because the RDW Gateway had the new certificate.
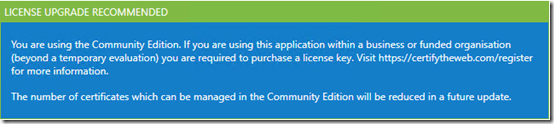
I followed the suggestion to update the program and now have a new message:
I do use it for business, and I believe in adhering to licensing requirements. Following that link. I see that they want $49.99 per year to manage the free Let’s Encrypt certificates for one server. I’m not sure how they justify that price, considering you can buy a 5-year Comodo PositiveSSL for $3.44 per year.
I decided to try the free mydomain.remotewebaccess.com from Microsoft again. If that continues to cause the problems I had before, I’ll buy a certificate. Either way, it will be nice to only have to worry about the certificate once per year, if that.