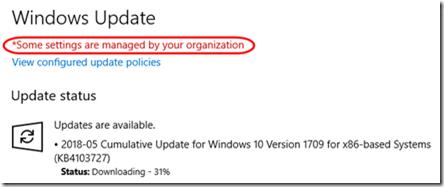
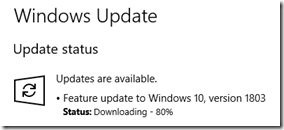
A Windows 10 Pro machine unexpectedly updated from 1709 to 1803, even though it is on a domain with group policy to defer updates. The Microsoft product team reviewed logs and informed me that 1803 was offered on May 12 but the machine didn’t get the deferral policy until May 15. What happened?
This machine is connected to a Windows Server 2016 DC running the Essentials role and backing up daily. I restored the full image from May 6 and started researching its status.
TL;DR The deferral group policy had not applied as of May 6. Even though the machine was domain-joined, group policy stopped working on February 14 because the NIC was not recognized with a Domain profile. Once I got the NIC back on the domain, 1803 stopped downloading.
The system probably applied KB4074588 on February 14 and rebooted itself. After that, the NIC was no longer domain-authenticated. It is unclear whether that is an issue with that update, or with Network Location Awareness in general (as blogged here).
2018 Timeline
I restored the system to its May 6 state (details below). Tracking back through the event logs, I worked out this timeline:
Feb. 6 1:58pm – Machine first set up, network category “Domain Authenticated”
Feb 13 – Cumulative Update KB4074588 released
Feb. 14 5:44pm – Machine restarted itself due to a “service pack update,” probably KB4074588.
Feb. 14 5:47pm – Network lost “Domain authenticated” status; came back up as “Private”.
Feb. 14 2:48pm – “The processing of Group policy failed because of lack of network connectivity”
Feb. 19 – I created and deployed deferral policies as blogged here.
Apr. 16 11:12am – Network now shows as “Public”, does not revert back to “Private”.
Jun. 2 12:03pm – Network once again “Domain Authenticated” after disjoining and rejoining domain. Group policy updates working.
Jun. 2 12:14pm – Group policy succeeded, adding new settings from 2 Group Policy objects.
Here are the relevant event logs entries:
Log Name: Microsoft-Windows-NetworkProfile/Operational Source: Microsoft-Windows-NetworkProfile Date: 2/6/2018 1:58:25 PM Event ID: 10000 Task Category: None Level: Information Keywords: (35184372088832),(32) User: LOCAL SERVICE Computer: WIN10-MACHINE Description: Network Connected Name: mydomain.local Desc: mydomain.local Type: Managed State: Connected,IPV4 (Internet) Category: Domain Authenticated Log Name: Microsoft-Windows-NetworkProfile/Operational Source: Microsoft-Windows-NetworkProfile Date: 2/14/2018 5:45:57 PM Event ID: 10001 Task Category: None Level: Information Keywords: (35184372088832),(32) User: LOCAL SERVICE Computer: WIN10-MACHINE.mydomain.local Description: Network Disconnected Name: mydomain.local Desc: mydomain.local Type: Managed State: Disconnected Category: Domain Authenticated Log Name: System Source: User32 Date: 2/14/2018 5:44:02 PM Event ID: 1074 Task Category: None Level: Information Keywords: Classic User: SYSTEM Computer: WIN10-MACHINE.mydomain.local Description: The process C:\Windows\system32\svchost.exe (WIN10-MACHINE) has initiated the restart of computer WIN10-MACHINE on behalf of user NT AUTHORITY\SYSTEM for the following reason: Operating System: Service pack (Planned) Reason Code: 0x80020010 Shutdown Type: restart Comment: Log Name: Microsoft-Windows-NetworkProfile/Operational Source: Microsoft-Windows-NetworkProfile Date: 2/14/2018 5:47:01 PM Event ID: 10000 Task Category: None Level: Information Keywords: (35184372088832),(32) User: LOCAL SERVICE Computer: WIN10-MACHINE.mydomain.local Description: Network Connected Name: Network Desc: Network Type: Unmanaged State: Connected,IPV4 (Internet) Category: Private Log Name: System Source: Microsoft-Windows-GroupPolicy Date: 2/14/2018 5:48:40 PM Event ID: 1129 Task Category: None Level: Error Keywords: User: SYSTEM Computer: WIN10-MACHINE.mydomain.local Description: The processing of Group Policy failed because of lack of network connectivity to a domain controller. This may be a transient condition. A success message would be generated once the machine gets connected to the domain controller and Group Policy has successfully processed. If you do not see a success message for several hours, then contact your administrator. Log Name: Microsoft-Windows-NetworkProfile/Operational Source: Microsoft-Windows-NetworkProfile Date: 6/2/2018 12:03:36 PM Event ID: 10000 Task Category: None Level: Information Keywords: (35184372088832),(32) User: LOCAL SERVICE Computer: WIN10-MACHINE.mydomain.local Description: Network Connected Name: mydomain.local Desc: mydomain.local Type: Managed State: Connected,IPV4 (Internet) Category: Domain Authenticated Log Name: System Source: Microsoft-Windows-GroupPolicy Date: 6/2/2018 12:14:03 PM Event ID: 1503 Task Category: None Level: Information Keywords: User: mcbsys\MarkAdmin Computer: WIN10-MACHINE.mydomain.local Description: The Group Policy settings for the user were processed successfully. New settings from 2 Group Policy objects were detected and applied.
What to Do
If you rely on group policy to distribute deferral policy, make sure group policy is working:
- Confirm the active network profile is Domain. If you have an RMM tool, you can use the script I wrote to check the firewall profile, which is also the network profile.
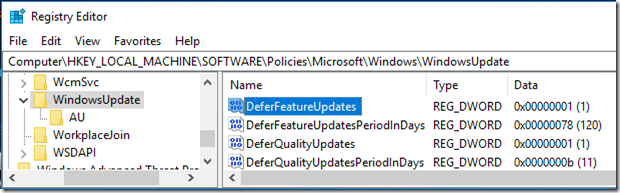
- Confirm that the expected registry entries have been created. in particular
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\DeferFeatureUpdates
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\DeferFeatureUpdatesPeriodInDays
This could also be scripted.
Initial Troubleshooting
For reference, here’s the step-by-step of what I found after restoring the May 6 image of this machine.
After connecting to the machine from the Hyper-V host and pressing Ctrl-Alt-Del, the initial logon screen shows _clientsetup_$, quite possibly the last user to log in “locally” as I usually use RDP for VMs:
After clicking Other User, I get a normal, domain login screen, so it’s definitely on the domain:
Remote access to the machine from Group Policy and regedit is not working (“RPC server is not available”).
RDP logon as domain admin fails (error 519).
Local logon from Hyper-V works, asks about network discoverability:
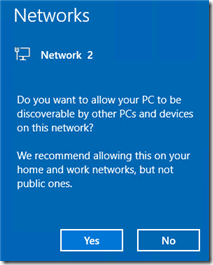
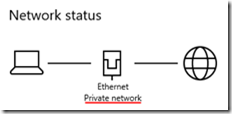
After clicking Yes, it says I’m on a Private (not Domain) network:
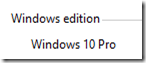
We’re definitely on Windows 10 Pro 1709:
![]()
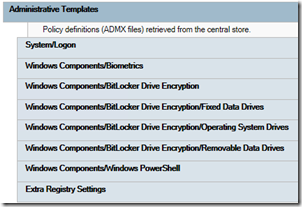
GPResult show that the Windows Components/Windows Update/Windows Update for Business group policy objects are NOT shown:
The registry is missing the Update for Business keys:
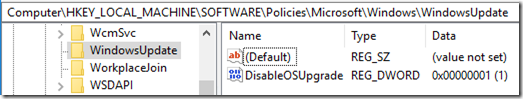
Ran gpupdate /force but the update failed “because of lack of network connectivity to a domain controller.”
No wonder the updates was not deferred. Sure enough, 1803 is downloading; it’s a race against time!
After disabling and re-enabling the NIC (and a long time “Identifying”), I have an “unauthenticated” domain connection, whatever that means:
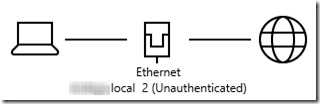
But it’s back to “Public”:

This long thread suggests disjoining and re-joining the domain to get the network authenticated. (I’ve had to do that before when restoring a system image—a little surprised it let me log in at all.) After the dis-join and re-join (and the two reboots required), the network is on the domain:
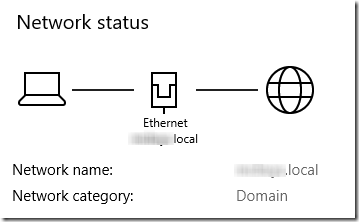
The deferral policies have been applied:
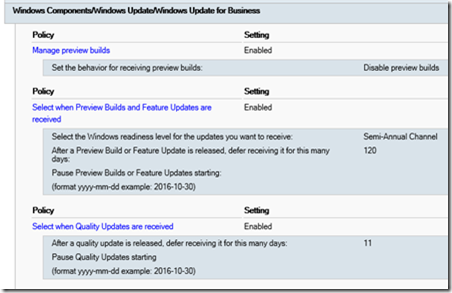
The registry entries are present:
And the 1803 update has been cancelled with only the latest cumulative update downloading (note the reference to group policy management of updates):