I installed Server 2016 Standard with the Essentials role about three months ago. I set up mydomain.remotewebaccess.com in the Anywhere Access Wizard. It automatically revoked a certificate with the same name issued to my previous 2012 R2 Essentials server.
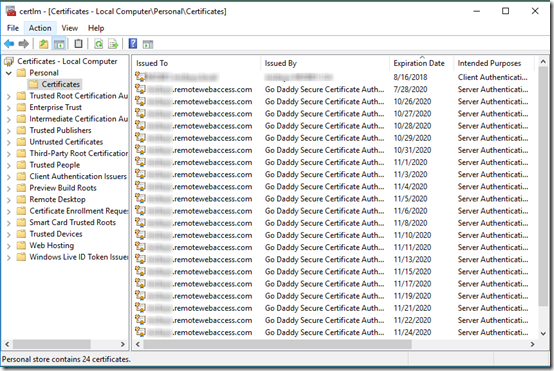
Now I see that it is installing a new certificate every one or two days:
Others have reported that the VPN stops working every couple days (see this thread). This is suspiciously close to the timing of the certificate re-generation.
I’ve been through extensive troubleshooting of this issue on a public Microsoft forum (see this thread) as well as a private Microsoft Partner forum.
More Information
You can follow the certificate re-issuance in the following log file on the server:
C:\ProgramData\Microsoft\Windows Server\Logs\SharedServiceHost-ManagementServiceConfig.log
or sometimes
C:\ProgramData\Microsoft\Windows Server\Logs\SharedServiceHost-ManagementServiceConfig.2.log
Here is an excerpt showing that the server failed to find the installed certificate:
[16980] 170920.093116.7200: DomainManager:CheckCertificateExpirationTask: CheckCertificateExpirationTask action called
[16980] 170920.093116.7200: DomainManager:CheckCertificateExpirationTask: Certificate expiration threshold: 30.00:00:00
[16980] 170920.093116.7200: DomainManagerObjectModel: DomainMaintenanceManager ctor called. InstanceID=513317
[16980] 170920.093116.7200: DomainManager:DefaultCertificateServiceProvider: IsCertificateNearExpiration called for domain mydomain.remotewebaccess.com with threshold 30.00:00:00
[16980] 170920.093116.7200: DomainManager:DefaultCertificateServiceProvider: FindCertificateForDomain called for domain mydomain.remotewebaccess.com
[16980] 170920.093116.8449: DomainManager:DefaultCertificateServiceProvider: IsCertificateNearExpiration: did not find a certificate, returning null
[16980] 170920.093116.8449: DomainManager:DefaultCertificateServiceProvider: FindCertificateForDomain called for domain mydomain.remotewebaccess.com
[16980] 170920.093116.8449: DomainManager:CheckCertificateExpirationTask: Certificate reported as expired, calling expiration handler
[16980] 170920.093116.8449: DomainManager:Service: CertificateExpirationHandler: trusted cert near expiration, will submit renew request
A Registry Fix
You can stop the re-issuance by setting HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Server\Domain Manager\ActiveConfiguration\ManualModeEnabled = True. However, according to this article, that also disables Dynamic DNS updates, which is not good. Microsoft Partner Support was unable to find any further information on what this registry value does.
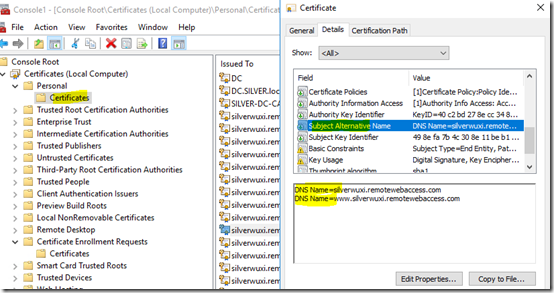
Subject Alternative Names
In most cases, certificates are only re-issued when the existing certificate has two Subject Alternative Names:
As I understand it, when deciding every two days whether to request a new certificate, the server looks in the certificate store for an existing certificate named xxxx.remotewebaccess.com. Somehow the presence of the extra SAN starting with www. causes this search to fail, so, thinking no certificate is present, the server requests a new certificate.
What is not clear is whether this is an issue in the server or at Go Daddy:
- I haven’t examined the Certificate Signing Request (CSR), but support tells me that it does not specify a SAN. Maybe if the server explicitly requested only one SAN, it would not get the extra one.
- Or maybe Microsoft could just ask Go Daddy to skip adding the “free’ www. SAN to certs for the remotewebaccess.com domain.
Regardless, the server logic should be corrected so that it inspects all SANs when searching for an expected certificate. Then it would not matter if Go Daddy added the www.
Caveats and Confusion
The user larsa001 reported in this thread that while most of their Essentials servers, including both 2012 R2 and 2016 editions, started getting double SANs and then re-generating certificates sometimes after April 2017. (In fact, according to this thread, there was a change in Go Daddy certificate issuance in June 2017, though it’s unclear what the problem was and what changed.) However, larsa001 notes on November 3, 2017 that they have one 2012R2 server with two SANs that is not re-generating certificates.
And my problem server suddenly stopped re-generating certificates on October 25. I have no idea what changed. The most recent certificate has two SANs.
Workaround, No Solution
The only sure workaround is to abandon the free xxxxx.remotewebaccess.com process and either go back to self-signed certificates (complicated but free) or buy a certificate from a trusted CA (starts at $5/year through resellers).
Microsoft Partner Support has duplicated the issue but are unable to escalate it internally for a fix. They suggested that I open a $499 phone incident and start troubleshooting from scratch. If phone support concludes that it is indeed a bug, the incident would not be charged. It’s unfortunate that Microsoft does not empower its partner support department to work issues through to resolution.
Update March 13, 2019 – Certificate Revoked without Replacement
This problem seemed to go away for a while–I stopped getting a new certificate every two days– but now it looks like that’s because renewal was failing. A few days ago, the working, non-expired certificate was revoked by Go Daddy with no replacement issued. More about that in this post: https://www.mcbsys.com/blog/2019/03/more-essentials-certificate-woes/.

I also come over this at a customers installation. Thanks for investigating!
Had this problem today on client installation. Thanks for the information!